repost from the creed community
You’ve probably seen the twitter threads of web3 detectives & sleuths diving in when a hack just happened. No-one knows what happened, the protocol team is scrambling to figure things out, and these online detectives are dropping threads explaining exactly how the hack went down. Pretty cool right? I thought so too! I wanted to know how these people do it, so I looked at the different tools they use and in this post I’ll give you a rundown of the tools used by the best web3 Sleuths.
Phalcon
https://phalcon.xyz/main goal: what happened during this transaction?supported chains: Ethereum, Binance Smart Chain, Polygon, Arbitrum, Cronos, Avalanche and FantomUX: ⭐️⭐️⭐️⭐
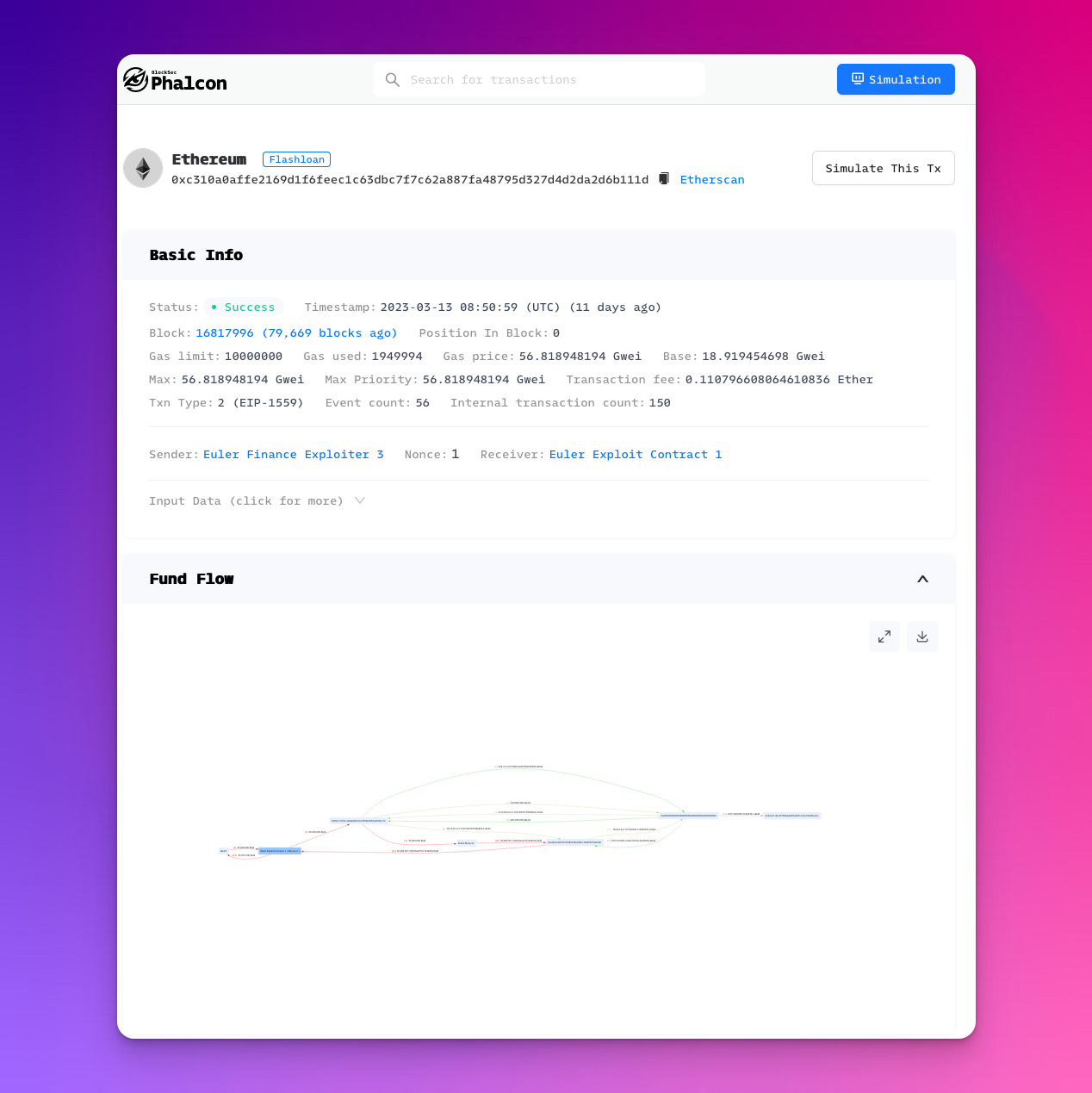
I’m particularly a fan of the ability to label, and colour different aspects in the Invocation flow. A feature which is incredibly useful when you’re reverse engineering the low level execution, and figuring out what’s happening.
Feature set:
- Transaction Info Summary
- Balance Changes Summary
- Fund Flow (as a diagram)
- Transaction Trace Exploring ( with debugging capability )
- Code View
https://blocksecteam.medium.com/getting-started-with-phalcon-2-0-253da584ca91
https://docs.blocksec.com/phalcon/introduction
MetaSleuth
https://metasleuth.io/main goal: assist user in figuring out relation between addresses and accountssupported chains: Ethereum, Binance Smart Chain, Polygon, Arbitrum, Cronos, Avalanche Moonbeam, Optimism and FantomUX: ⭐️⭐️⭐️⭐️
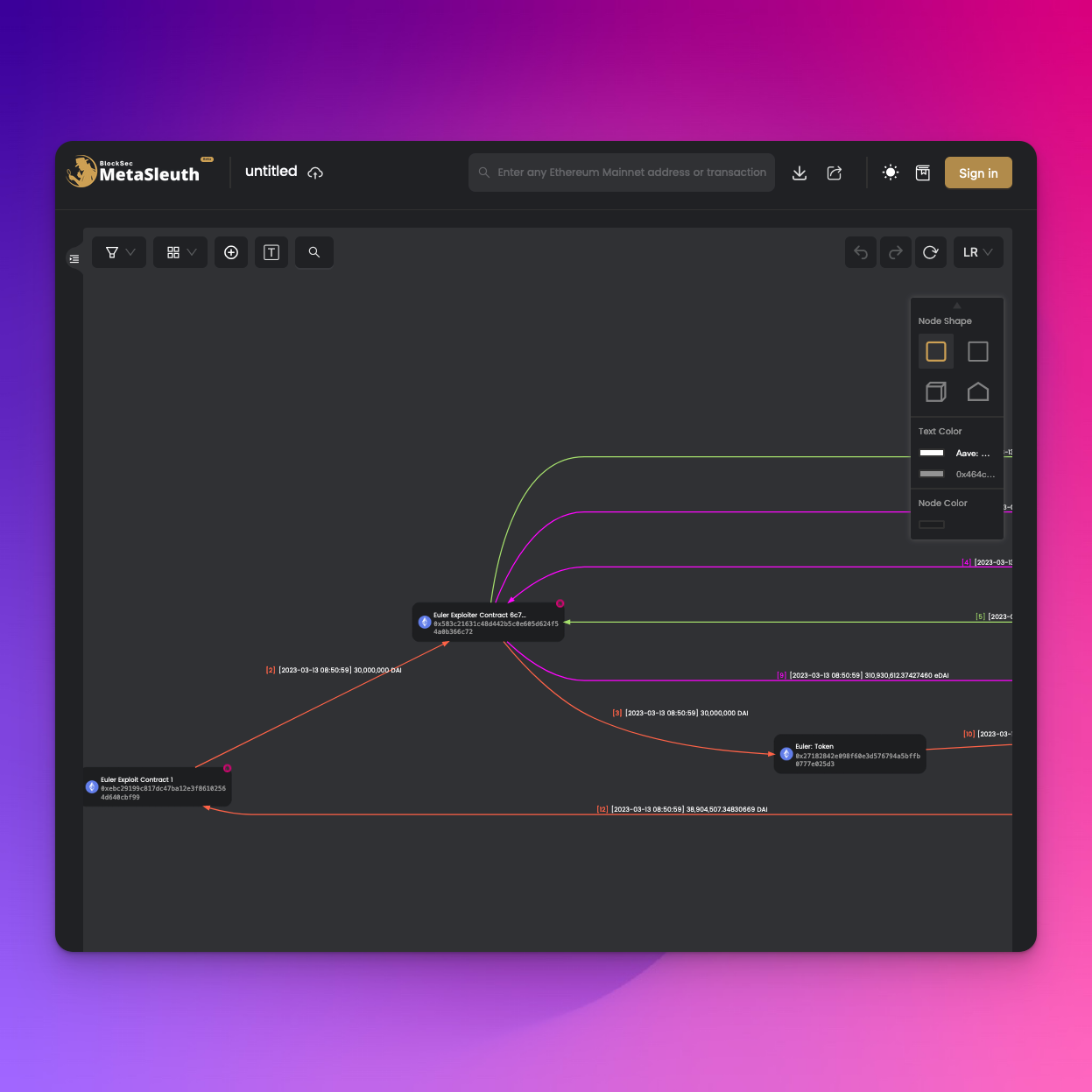
Similar to Phalcon, MetaSleuth doesn’t just provide visualization. You have various features in the Metasleuth interface that allow you to customize graph nodes, labels and node names. This can help a lot when you’re still trying to understand what happened and trying to get an organized overview!
I really like being able to pick one transaction / address to explore, and then iteratively exploring the associated addresses and transactions. This can be particularly helpful when there are multiple contracts, or multiple exploit transactions!
Feature set:
- Fund Flow (as a diagram)
- Suggested related addresses
- Cross-chain analysis
- etc.
https://metasleuth.io/https://docs.blocksec.com/metasleuth/introductionhttps://docs.blocksec.com/metasleuth/introductionhttps://blocksecteam.medium.com/metasleuth-how-to-use-metasleuth-to-analyze-a-phishing-attack-b525caac14c5
Transaction tracer
https://openchain.xyz/tracemain goal: quick summary of what happened during the transactionUX: ⭐⭐⭐ ( minimalistic 👍)
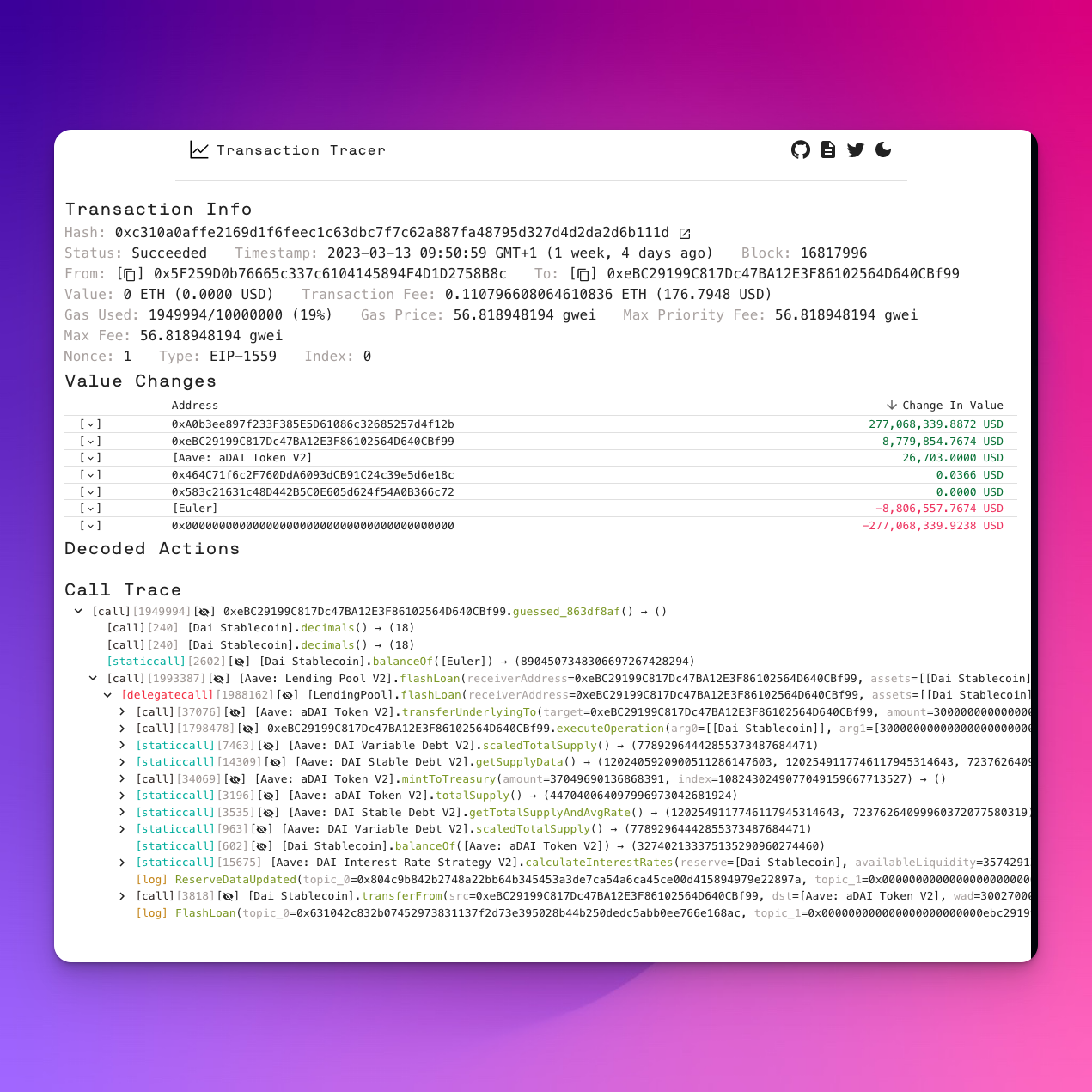
It’s simplicity is both the strength and weakness of the platform, so I’ll personally will use it in addition to but not as a replacement of any other tool in this list.
Feature set:
- Transaction Info Summary
- Balance Changes Summary
- Transaction Trace Exploring
ethtx
https://ethtx.info/UX: ⭐⭐⭐goal: turn transaction into human readable database of useful info
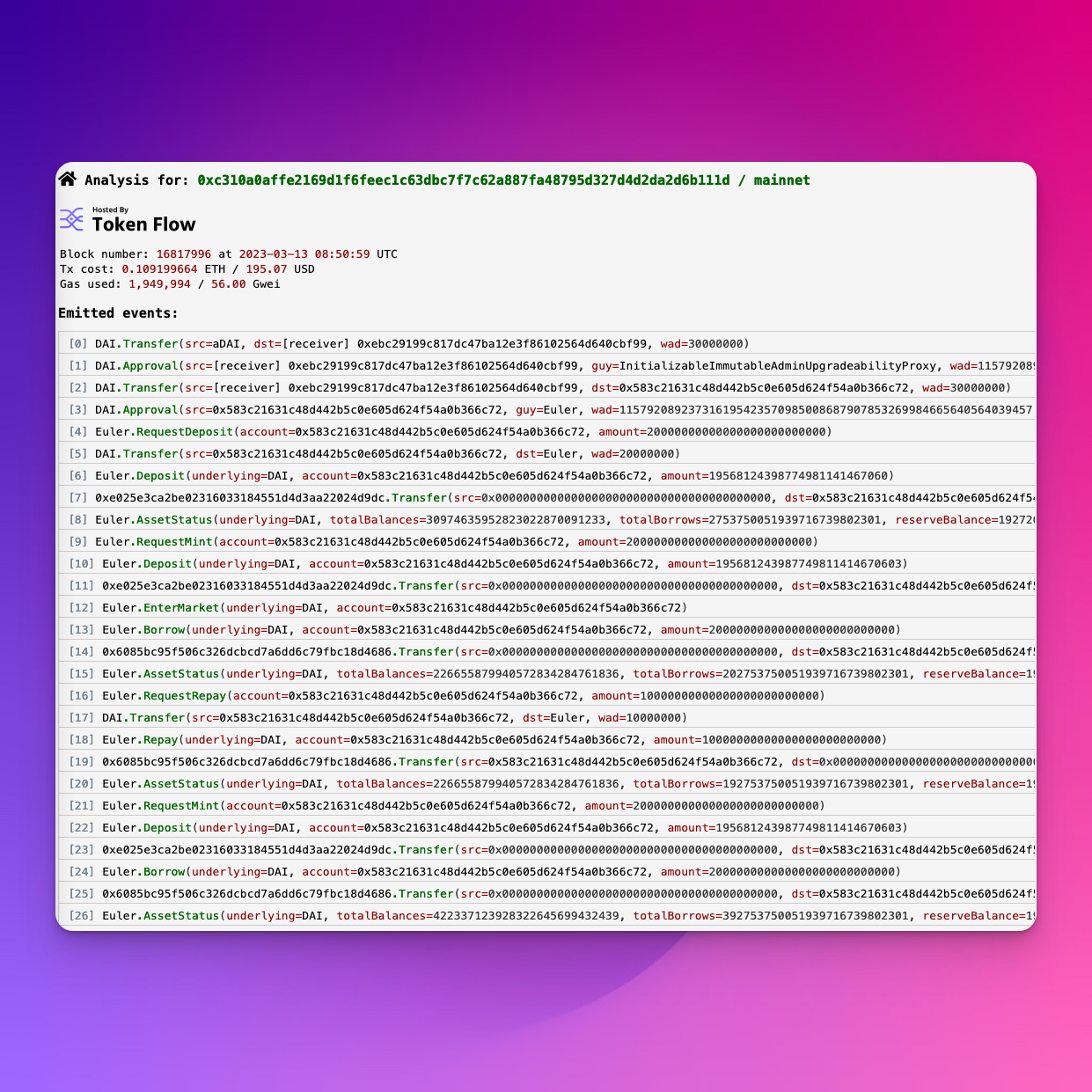
- Transaction Info Summary
- Events Emissions
- Balance Change Summary
- Token Transfers
- Transaction Trace Exploring
Tenderly
https://dashboard.tenderly.co/explorergoal: understand the code being hackedUX: ⭐⭐⭐⭐
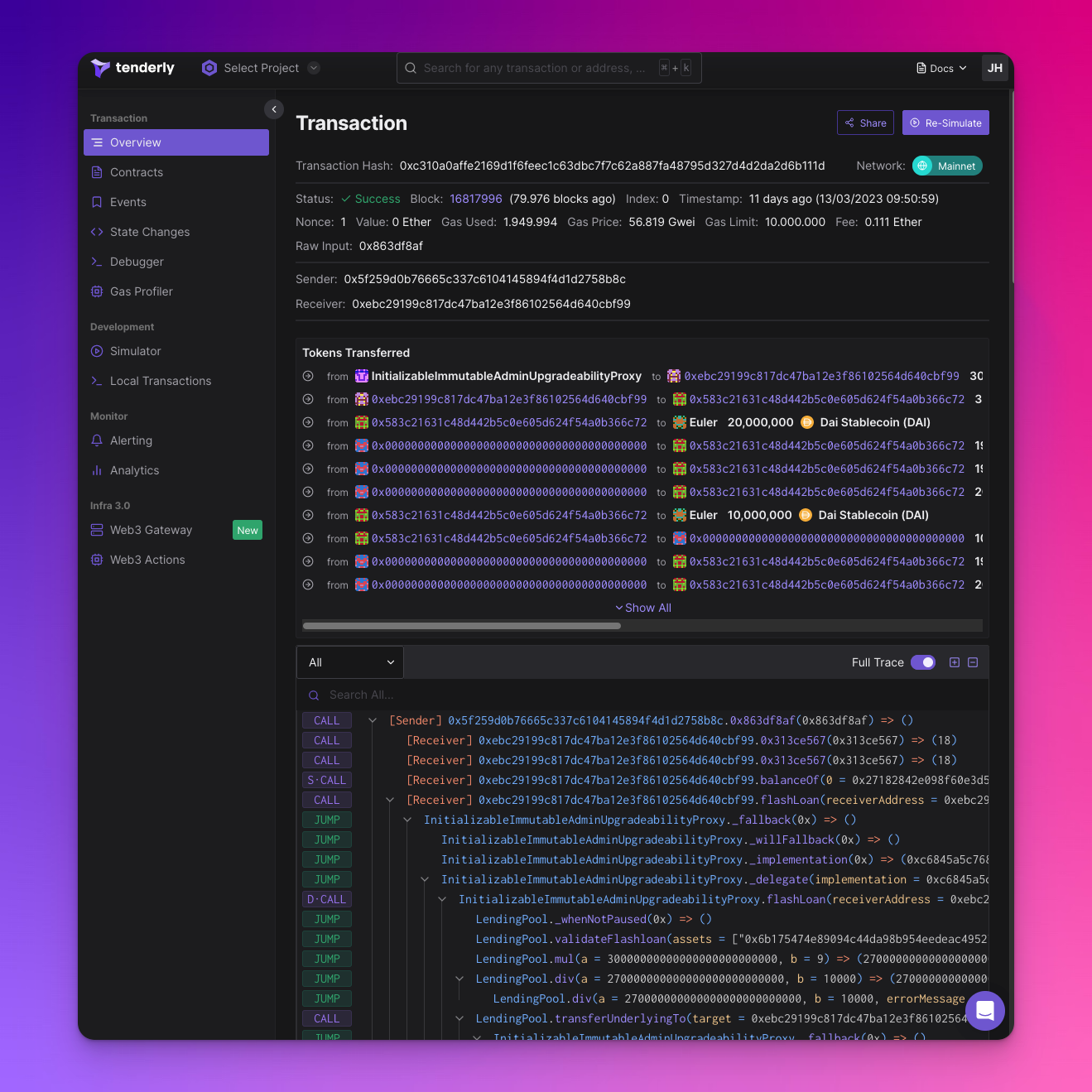
If I had to describe the difference between Tenderly and some of the other tools, I’d say that other tools can help you understand the hack, Tenderly helps you understand the code that’s being hacked.
Feature Set:
- Transaction Info Summary
- Events
- State Changes
- Token Transfers
- Transaction Trace Exploring
- Debugging with extensively configurable re-simulation
- Code Explorer
Others
Other tools you might like to check out:
- eigenphi - Nice step-through experience for flow of funds diagram.
- cruise - Similar to Transaction Tracer.
- etherscan - Not aimed at sleuthing, still damn usefull
- icevision.xyz - Nice transaction flow exploration.
Summary
In the future I’ll be using a combination of these tools, with a focus on three in particular:
- Phalcon - To distill what happened during an attack transaction.
- MetaSleuth - To explore the different contracts, accounts and flow of funds related to an attack.
- Tenderly - To explore the execution trace of an attack transaction.
I’ve probably missed some tools, so feel free to comment with the ones you like!